Last time, we discussed the basic division of electronic warfare into Electronic Signal Measures (ESM, detection of enemy electronic signals), Electronic Countermeasures (ECM, use of active measures to mess up enemy signals) and Electronic Counter-Countermeasures (ECCM, techniques to defeat enemy ECM), and how ESM works. This time, we'll look at the area most people think of when they talk about electronic warfare, ECM.

A radar screen showing the effects of jamming
The most basic ECM technique is simple noise jamming. This is flooding a relevant portion of the electromagnetic spectrum with white noise, with the intent of drowning out the relevant signal. For a radio, it's the equivalent of trying to talk while someone blasts loud music, and the same principle applies to radar, reducing the range at which a radar unit can get a useful return.1 Noise jamming is usually divided into a few categories, spot, barrage, and sweep. Spot jamming is transmission on a specific frequency, which is highly effective if the system in question is limited to only a single frequency.2 However, most modern radars are "frequency agile", which means they can switch away from a jammed frequency to any of a great number of other frequencies. One way to counter frequency agility is to jam the entire band the radar could be operating in, known as barrage jamming. The problem with barrage jamming is that it is rare to find a jammer powerful enough to be able to blanket a wide spectrum. Sweep jamming, where the jammer's power is swept across a variety of frequencies, is capable of defeating electronics with poor error-checking, although it's not particularly useful against better-designed systems.

A Lancaster bomber drops Window
The other simple form of ECM is the physical decoy. The most famous version is chaff, originally known as Window by the British3 and developed during WWII. Chaff, essentially strips of aluminum foil cut to the length to make them ideal radar reflectors, was dropped from airplanes to create false targets and noise on the screens. When it was first used by the RAF during a raid on Hamburg on July 25th, 1943, only 12 of the 791 aircraft involved in the mission were shot down, a quarter of the casualties normally expected from a raid of that size.4 Later, most warships were fitted with chaff launchers, which created false targets for anti-ship missiles, such as the SRBOC launchers aboard Iowa. While it is highly effective against older systems, the lack of motion makes it easy for sophisticated sensors to discriminate chaff clouds from actual targets. Chaff is often used together with flares, which serve much the same role in the infrared portion of the spectrum. These brightly-burning pellets will hopefully prove a more attractive target to an incoming missile and draw it off. Most older IR-homing missiles have only a narrow field of view and are unlikely to reacquire a target that is lost, while modern weapons have systems to recognize and ignore flares. Other physical decoys use corner reflectors to increase their apparent size to radar.
Other decoys are more sophisticated, attempting to produce a signature that closely mimics a real target. A typical example is a sophisticated transponder that amplifies and repeats incoming radar signals. This device, known as a "blip enhancer", creates a false target on the enemy radar screen, or makes an existing one bigger. An early application was to disguise the location of an aircraft carrier by increasing the signature of its escorting destroyers to match. During the Falklands War, the British used helicopters fitted with blip enhancers to mimic ships, hoping to draw off Exocets, a technique also used by the modern Nulka decoy. Other uses include turning a small missile into a bomber to confuse air defenses. Some aircraft even use a towed blip enhancer to draw off missiles that have been programmed to ignore non-moving targets such as chaff.
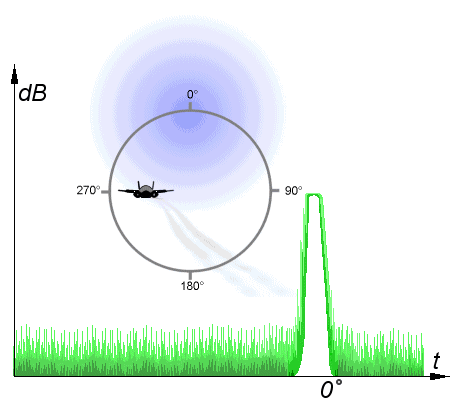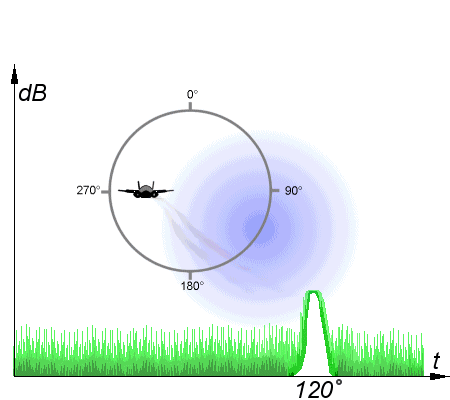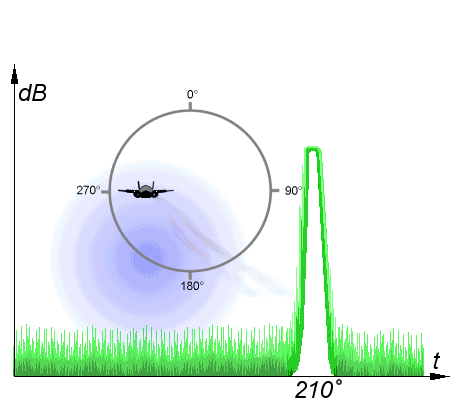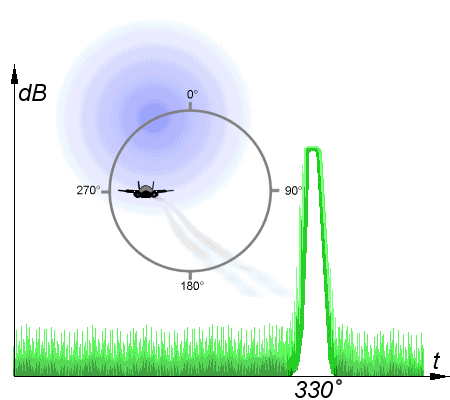
Conical scanning
But the most interesting of ECM techniques is deception jamming. Instead of attempting to flood a radar with energy, these methods transmit specific signals that interfere with specific features of the radar. One of the first of these was angle stealing against conical scan radars. A conical-scan radar works to increase the accuracy of a radar by rotating the signal lobe, offset at a slight angle, around an axis. If the target is not on the axis, the received signal will be strongest when the beam is pointed towards the target, and weakest when it is on the other side of the scan. If the centerline is pointed directly at the target, then a constant signal is received. This makes it easy to automatically track targets, even with very primitive electronics. However, an attacker can transmit a different signal on the same frequency, with the peaks offset to indicate a different angle to the radar. The radar will then begin to track this false signal, deceiving the operator as to the target's location. Conical scanning was very common in early fire-control radars, but is rare today because of how easy it is to jam.

Countermeasures pods in the National Electronics Museum
A related technique, range gate pull-off, is effective against many more modern track-while-scan radars. These radars use a range gate to track targets, filtering out all signals that are more than slightly different from the last position of the target, and adjusting the gate with each scan to maintain the track. An airplane attempting to pull off a range gate uses a transponder very similar to a blip enhancer to re-transmit a stronger version of the incoming radar signal. Initially, the resulting echo is within the range gate on the airplane, but over time, an increasing delay is set between the arrival of the signal and the transponder's echo. The range gate follows the stronger signal, allowing the aircraft to slip out and break the lock. A similar technique, velocity gate pull-off, uses a signal shifted in frequency instead of time against Doppler radars.6

An AGM-88 High-speed Anti-Radiation Missile (HARM) under the wing of an F/A-18C
The last area traditionally under the purview of ECM is physical attacks directed specifically at electronic systems. The most common of these is the anti-radiation missile, a group of weapons designed to home in on radar sites and other transmitters. These originated during the Vietnam War, when the US needed a way to destroy enemy SAM radars, and developed missiles that would track them down and destroy them. The USN equipped their normal fighters with ARMs, while the USAF created special squadrons known as Wild Weasels for the job. Early ARMs would go blind if the target radar was shut down, but modern versions have various means of compensating for this. Some remember the location of the radar and continue to seek in on it, while others deploy parachutes and wait for the radar to come back on. A similar technique is sometimes used to counter jamming by homing in on the ship or airplane emitting the jamming signal.
ECM is a weird and fascinating world, and I've only scratched the surface. But the development of these countermeasures was immediately matched by the development of counter-countermeasures, which I will discuss next time.
1 The strength of a returned radar signal is inversely proportional to the fourth power of range, while that of a jammer obeys the inverse square law, so totally blocking a radar is usually not feasible, and at some point the radar will burn through the jamming and be able to see targets close in. ⇑
2 Early spot jammers had only very limited tuning capability, requiring a great number for effective use, such as those countering German guided bombs. Later, a type of tube known as the carcinotron was developed which could vary its frequency across a wide band. ⇑
3 So named because a scientist, told that the code-name must bear no relation to the device, looked around and said "Why not call it window?" ⇑
4 Unfortunately for Bomber Command, the Germans rapidly developed new tactics which greatly reduced the effectiveness of Window, focusing on steering the pilots into the bomber stream and letting them find their own targets. ⇑
5 Author's photo. ⇑
6 Doppler radars use the Doppler effect, the change in frequency of the reflected signal due to the velocity of the target, to measure the target's velocity and discard stationary targets. ⇑


Comments
One of the advantages of a stealth aircraft (or ship I suppose) is that because the reflected signals are much weaker, it it possible to manipulate the signal with a much smaller energy output.
So your angle gate and range gate trickery can work without the aircraft having to broadcast a strong signal, which clearly would have its own risks, dangers and expenses.
While that's true, I'm not sure how applicable it is. The power necessary for that kind of deception jamming isn't that high, simply because there's a lot of space and not a lot of plane, so the amount of energy hitting the plane isn't large. By the era where stealth becomes an actual thing, that kind of deception jamming is a lot less common. And by the time you're in a position to use deception jamming, avoiding active emissions usually isn't that big of a concern, because the enemy already has you.